Quick Connect Help
Quick Connect provides an alterative to a Full Profile. The dialog is simplified (it provides fewer options) and avoids the necessity of creating a Profile. If the connection is unlikely be used again this feature is probably the best (certainly the least typing/clicking) option. The disadvantage is that the information is discarded when the connection is terminated and it does not appear in the Recent Connections list which can greatly speed up connection to regular services.
When the Quick Connect tab is selected it reveals two further tabs Connection Details and Options. Connection Details is initially selected:
Connection Details
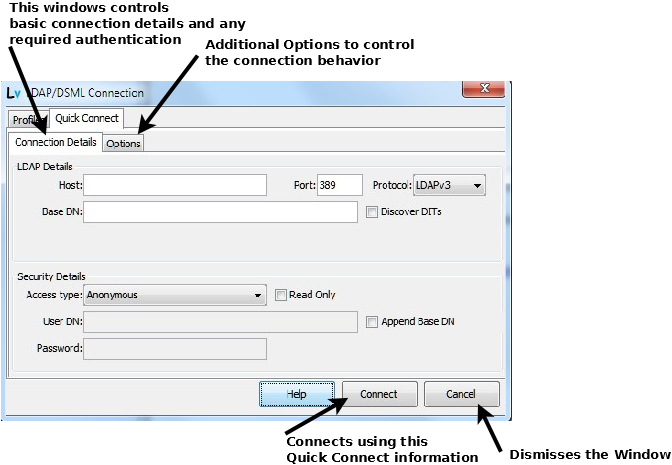
You need only enter as much information as required to initiate the connection. A connection may be, depending on its complexity, accomplished using a small subset of the total information. This Window is organized into two sections: LDAP Details: describes the physical connection and Security Details allows selection of the security type and capture of any required credentials. The purpose and usage of each field is described below (left to right, top to bottom).
- Host: The host name of the server providing the target LDAP service. For example, localhost (if the LDAP server is on this machine) or ldap.example.com or fred.example.org if the server is remote. There is no need to add any protocol identifier such as ldap://, ldaps:// or http:// (for DSML). The appropriate value will be added by LDAPviewer. Note: When using any TLS/SSL service the hostname must be the same as appears on the cn= value of the subject (or subjectAltName). For example, if the LDAP server is running on the same server (normally localhost would be permissable) but has a certificate whose subject attribute has a value of cn=ldap.example.com then ldap.example.com must appear in the Host field not localhost.
- Port: The port number used by the LDAP service. LDAPviewer defaults to port 389 but this can be changed for all Profiles and the Quick Connect service by selecting Preferences from the Options Menu.
- Protocol: Select the required protocol from the drop down conbo box:
- LDAPv3 LDAP version 3 (default - this can be changed at Preferences). This is the current and most common protocol supported by LDAP servers including MS Active Directory.
- LDAPSv3 LDAP version 3 using TLS/SSL. Selecting this type will generate an LDAP URL of the form ldaps://hostame:port. By convention, LDAPSv3 is supported on port 636 but any port may be configured by the LDAP server's administration staff to support this service and the user is reminded to verify, and change as necessary, the Port: field. Selecting the LDAPSv3 option automatically adds TLS to the Access Types: below. You may want to read more about LDAPviewer's flexible TLS/SSL support.
- LDAPv2 LDAP version 2. An older and much less common protocol supported by certain servers.
- DSMLv2 Directory Services Markup Language version 2 (essentially an XML wrapper for LDAP). Selecting DSMLv2 will make visible an additional DSML Service: field.
- Base DN: This defines the lowest DN that LDAPviewer will attempt to read. For example, if using standard RFC 2247 style naming this may be a suffix of the form dc=example,dc=com, if using X.500 style naming it may be a suffix of the form o=corp,c=my. It is perfectly legitimate, however, to use any value as a Base DN: not just the LDAP suffix. Thus, if a user only has permission to access a part of the DIT such as that commencing ou=people,dc=example,dc=com or ou=people, ou=calgary,dc=example,dc=com then this should entered in the Base DN field. LDAPviewer will make no attempt to read entries below this DN. Conversely, if an organization uses X.500 style naming of o=corp,c=my but uses a suffix of c=my then this value (or o=corp, c=my) is a perfectly valid Base DN. Leaving the Base DN: blank will cause LDAPviewer to read the RootDSE entry (which may require authentication on some LDAP servers). (Full Profiles allow the option to permanently display the RootDSE during a connection.) The DIT for this base DN is displayed in the Primary DIT pane of the LDAPviewer window.
- Discover DITs: Checking this box will cause LDAPviewer to discover all the available DITs by reading the RootDSE and all its supported namingContexts attributes (the DIT suffixes). All the available DITs are displayed in a single tree structure. If authentication is required to access RootDSE then the details should be entered in the Security Details section. If additional authentication is required for access to any DIT then a Full Profile should be used for this purpose. If, however, Anonymous access allows reading of all DITs, the Quick Connect provides this capability. When Discover DITs: is checked the value of any Base DN is ignored. Assuming anonymous read access to the RootDSE and all the DITs, simply enter the Host:, click Discover DITs: followed by the Connect button. This is the quickest of the Quick Connect options.
- DSML Service: This field is only visible if DSMLv2 has been selected as the Protocol: and is invisible at all other times.
DSMLv2 service is typically provided at a URL which consists of the Host: and suffix of the form dsml/service/at/url. Enter the full suffix in this field. LDAPviewer will open the DSMLv2 service at the URL http://hostname:port/dsml/service/at/url.
Clicking the Options tab will dirplay this Window:
Options Window
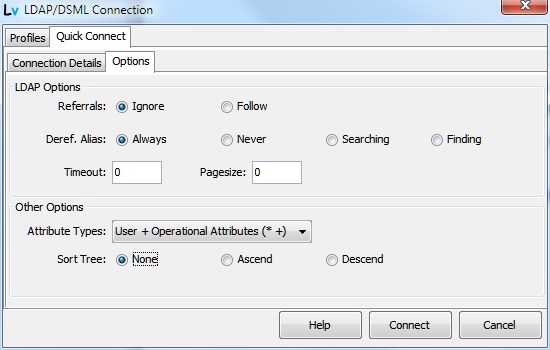
The Options Tab controls a number of features that affect the behavior of the LDAP/DSML connection. Each field is described (Left to Right, Top to Bottom).
- Referrals: This controls what the LDAP server will do when it encounters a referral objectClass in a read or search operation. Referrals are typically used when the DN addressing structure for any particular path (DN/RDN) is continued in another LDAP server (Referrals allow a full LDAP URI). Two options are available:
- Ignore Selecting Ignore (the default - which may be changed using the Options Menu, Preferences) will cause any referral objectClass encountered in a read or search path to be returned and treated as a non-referral. The server will not follow the URL/DN defined in the ref attribute of the objectClass. Selecting this option allows the referral objectClass and its associated attributes to be inspected and/or edited.
- Follow Selecting Follow will cause a referral objectClass, encountered in a read or search operation, to follow the URL/DN value defined in the ref attribute. The referral attribute is essentially invisible (its normal behavior in an operational DIT).
-
- Deref. Aliases: This option controls what the server will do when it encounters an alias objectClass. An Alias is typically used to change the resolution path of a DN/RDN to another location within the LDAP server (an alias only allows a DN not a full LDAP URI) by replacing (aliasing) one DN value for another. Deference Alias options only apply to search and read operations and do not apply to modify, add or delete (edit) operations. Four options are available:
- Always The LDAP server will always deference the alias, that is, it will substitute the DN defined in the AliasedObjectName attribute of the alias objectClass for the DN that was referenced in the search operation. This is the default option but may be changed in Preferences (Options Menu).
- Never The LDAP server will never deference the alias, that is, it will never substitute the DN defined in the AliasedObjectName attribute of the alias objectClass for the DN that was referenced in the search operation.
- Finding The LDAP server will deference any alias, that is, it will substitute the DN defined in the AliasedObjectName attribute of the alias objectClass for the DN that was referenced in the original operation but only during the name resolution of the search operation (establishing the search base DN), thereafter (on any found entry/entries) no dereferencing will be performed.
- Searching The LDAP server will never deference any alias, that is, it will not substitute the DN defined in the AliasedObjectName attribute of the alias objectClass for the DN that was referenced during the name resolution of the search path (establishing the search base DN). Thereafter (in the search results) all aliases will be deferenced (DN substitution will occur).
- Timeout: Defines the time in milliseconds before LDAPviewer will decide the LDAP operation has failed, a value of 0 (the default) indicates LDAPviewer will wait up to its normal limit of 5 seconds before determining an operation has failed.
- Pagesize: Defines the maximum number of entries that will be returned in any single search page. A value of zero (the default) indicates that the server will send the maximum number of search results determined by its configuration limits. In both cases LDAPViewer will continue to read from the server until all the results have been received. The only reason to not leave the field at is default value (0) is where there are limits in incoming block sizes at the LDAPviewer (or an intermediate) location.
Attribute Types: Defines the attributes to be returned on all read Entry operations and may be used to define a unique attribute set for the profile.
Note: Attributes are generically classified as user (they contain user data and depending on ACL permissions are typically editable) or operational (they contain data created and used by the LDAP server and are never editable by the user).
By default the drop-down menu provides three options:
- All-Attrs (* +) Indicates that both user and operational attributes will be returned on all Read Entry operations. This is the default but may be changed using Preferences (Options Menu). Any search requests may override this value.
- All-User (*) Indicates that all user attributes will be returned on all read Entry operations. Any search requests may override this value.
- All-Ops (+) Indicates that only operational attributes will be returned on Read Entry operations. Any search requests may override this value.
If the user has defined one or more Return Attributes Named Lists (using the Search menu) then these are also displayed in the drop-down menu and may be selected. If the Return Attribute Named List is modified the changes will be reflected on the next connection which uses the named list.
Note: The HTML Editor uses the user attribute objectClass to select appropriate templates. If only Operational attributes are selected or the attribute objectClass is not ncluded in the returned attributes then the default HTML template will be used to display the entry.
- Sort Tree: This option indicates whether sorting will occur in the DIT Tree Windows. The available choices are:
- None No Sorting will be done on any DIT Window. Attributes will be displayed in the order they are received from the LDAP server. This is the default option but may be changed using Preferences (Options Menu).
- Ascend Attributes will be displayed in ascending alphabetic order for all DIT Windows.
- Descend Attributes will be displayed in descending alphabetic order for all DIT Windows.
When the information has been entered click the Connect button to initiate the connection.




