Tech Stuff - Survival Guide to NTLM
This page collects some information on the workings of NT LAN Manager (NTLM). We concentrate on those things which are particularly useful when configuring Samba and specifically a Samba Primary Domain Controller (PDC). It is by no means complete - reflecting our normal knowledge state - but some bits may be useful.
Contents
Logon Process - local and global accounts and Groups
SIDs and RIDs and other gobbledygook
Standard Group Accounts
Mapping NT Rights to Groups
You can get a useful little command line utility that will display all kinds of SIDs etc on a windows machine.
Logon Process - local and global accounts and groups
The process of using domains in NT LAN Manager (NTLM) and the relationship between domain accounts and groups and local accounts and groups is shown below:
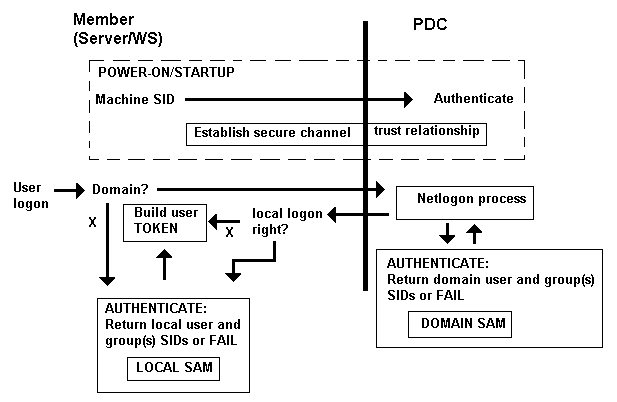
Notes:
SAM = Security Accounts Manager and is maintained in the registry under \HKEY_LOCAL_MACHINE\SAM - this cannot be read normally even as Adminstrator - but there are wheezes that will allow you to inspect the entries should you be overtaken by insatiable curiosity.
As soon as the PC is powered on the machine SID is used to establish a secure channel and trust relationship with the domain. The username is the machine name with an appended $ - thus if the name of the PC is MYPC then this account (the machine account - confusingly frequently termed the MAC) will be named MYPC$.
When a human being finally deigns to logon the resulting sequence will depend on whether the logon is local or using the domain:
Local logon: The LOCAL SAM is used exclusively to authenticate and creates a security token which contains the sum of all the rights obtained from the local account and its associated groups.
Domain logon: The logon information is forwarded to the domain (PDC - using the secure channel established by the machine SID authentication process) and authentication takes place against the DOMAIN SAM. The process returns the rights from the user account and its associated groups. If the rights include log on locally (and almost all standard groups include this right) then further authentication takes place against the LOCAL SAM and the resulting security token comprises the sum of domain and local rights (for both the user and associated group(s)). If the domain rights do not include log on locally or there is no local account then only domain rights are obtained.
SID and RIDs and other earth shattering stuff
The term SID (Security ID) is applied to machine accounts, user accounts and groups. RID ( Relative ID) defines one or more subauthority elements in the SID - it appears (we could find no definitive reference or definition) that each item separated by a dash in the authority section can be called a RID. The generic layout of the SID is:
S-R-I-A[-A...]
Where:
| Param |
Description |
Value(s) |
Notes |
| S |
Fixed Value |
S |
Identifies a SID. |
| R |
Revision |
1 |
Currently Fixed Value = 1 |
| I |
Identifier-authority |
0 = Null
1 = world (Everyone)
2 = local
3 = creator
4 = non-unique ID
5 = NT authority
|
- |
| A |
Subauthority |
0 = null
1 = dialup
2 = network
3 = batch
4 = interactive
5 = logon
6 = service
7 = anon logon
8 = proxy
21 = NT non-builtin IDs
32 = NT built-in
|
a.k.a. RID (Relative ID)
There may be one or more RIDs in a SID in the domain context there are 3 10 digit RIDs |
Examples:
S-1-1-0 = Null (Everyone)
S-1-5-21-1017080363-1132274894-948791989-500 = Administrator
S-1-5-32-545 = Users group (local)
S-1-5-32-1017080363-1132274894-948791989-513 = domain users
The currently logged in account is maintained in the registry under \HKEY_USERS.
Standard Group Accounts
The following are standard group accounts used by Windows servers (well NT4.0 anyway). Each group has an assigned set of rights. This MS Knowledge Article 243330 provides more information.
The column Samba with yes below indicates that this account is required in a pure Samba environment - one in which Samba is being used, say, as an NFS replacement and in which no Windows systems need be present. All the others are required (and possibly others) to map existing Windows accounts into the Samba system so that an NT/Win2K workstation can continue to use its well loved Group account names.
The accounts listed below are automagically created by an non-LDAP Samba3 implementation. The tools available with Samba3 (from IDEALX) create the accounts below with the addition of Domain Computers.
| Name |
SID |
Samba |
Notes |
| Replicators |
S-1-5-32-552 |
|
|
| System Operators |
S-1-5-32-549 |
|
workstation = Power Users |
| Guests |
S-1-5-32-546 |
|
|
| Domain Guests |
S-1-5-32-DOM0-DOM1-DOM2-514 |
yes |
|
| Domain Admins |
S-1-5-32-DOM0-DOM1-DOM2-512 |
yes |
|
| Power Users |
S-1-5-32-547 |
|
|
| Print Operators |
S-1-5-32-550 |
|
|
| Administrators |
S-1-5-32-544 |
|
|
| Account Operators |
S-1-5-32-548 |
|
|
| Backup Operators |
S-1-5-32-551 |
|
|
| Users |
S-1-5-32-545 |
|
|
| Domain Users |
S-1-5-32-DOM0-DOM1-DOM2-513 |
yes |
|
| Domain Computers |
S-1-5-32-DOM0-DOM1-DOM2-553 |
yes |
created by IDEALX LDAP smbldap-populate.pl script but not by tdbsam. |
Mapping of Groups to Rights
In a Windows domain system each standard group provides a number of rights as defined below:
| Right |
Users |
Administrators |
Backup Operators |
Server Operators |
Print Operators |
Account Operators |
Guests |
| Configurable Rights |
| Backup files |
- |
yes |
yes |
yes |
- |
- |
? |
| restore files |
- |
yes |
yes |
yes |
- |
- |
? |
| change system time |
- |
yes |
- |
yes |
- |
- |
? |
| access network |
yes |
yes |
yes |
yes |
yes |
yes |
? |
| log on locally |
- |
yes |
yes |
yes |
yes |
yes |
? |
| manage audit security log |
- |
yes |
- |
- |
- |
- |
? |
| shutdown-remote |
- |
yes |
- |
yes |
- |
- |
? |
| shutdown-local |
- |
yes |
yes |
yes |
yes |
yes |
? |
| add workstation |
- |
yes |
- |
- |
- |
- |
? |
| add/remove drivers |
- |
yes |
- |
- |
- |
- |
? |
| take ownership of files |
- |
yes |
- |
- |
- |
- |
? |
| Built-in (non-configurable) Rights |
| create/mod user accounts |
- |
- |
- |
yes |
- |
yes |
? |
| create/mod global groups |
- |
yes |
- |
- |
- |
yes |
? |
| create/mod local groups |
- |
yes |
- |
- |
- |
yes |
? |
| assign rights |
- |
yes |
- |
- |
- |
- |
? |
| lock server |
- |
yes |
- |
yes |
- |
- |
? |
| override server lock |
- |
- |
- |
yes |
- |
- |
? |
| format server hard disk |
- |
yes |
- |
yes |
- |
- |
? |
| create common groups |
- |
yes |
- |
yes |
- |
- |
? |
| keep local profile |
- |
yes |
yes |
yes |
yes |
yes |
? |
| share/unshare directories |
- |
yes |
- |
yes |
- |
- |
? |
| share/unshare printers |
- |
yes |
- |
yes |
yes |
- |
? |
Notes:
The seemingly innocuous log on locally right indicates that if there is a local account with the same credentials (username and password) then local properties (groups) are added to the domain properties. If this right is not present then the user has only domain rights and generally can only access anything with the Everyone group property on the local machine. You can, effectively, lock yourself out of your local machine with this right.
Samba Net Commands
The following are some of the new net commands in Samba 3.x. (see man net for full details).
| Cmd |
Params |
Notes |
| net getlocalsid |
[PDC Name] |
Displays the SID of the domain in format:
S-1-5-21-AUTH0-AUTH1-AUTH2
|
| net groupmap |
list |
Displays the name and SID of the groups available for the domain.
|
Local SID
To obtain the SID of a local machine (for the current logged in user) use:
# use regedit
\HKEY_USERS
# the final RID will indicate the user
To obtain the SID of a local machine (for the current logged in user) use:
# use regedit
\HKEY_USERS
# the final RID will indicate the user
More to Come - Under Construction
Problems, comments, suggestions, corrections (including broken links) or something to add? Please take the time from a busy life to 'mail us' (at top of screen), the webmaster (below) or info-support at zytrax. You will have a warm inner glow for the rest of the day.